Author's note: Technical standards are a discipline related to both technology and economics. A companion paper, "The Fundamental Nature of Standards, Economic Perspective," was presented in the International J.A. Schumpeter Society Economics Conference, June 28 - July 1, 2000, Manchester, England
____________
Computer viruses are an example of how technical standards can support a life-like phenomena. Virus is the term for a very simple life form. Computer viruses can mimic life and exist by replicating over the Internet, a network based on Internet Engineering Task Force (IETF) standards or over a specific operating system or specific program. Without common systems of some kind, computer viruses, as we currently understand them, could not occur.
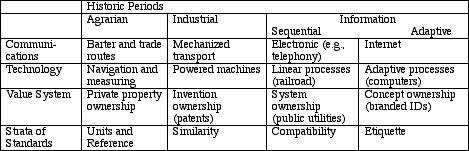
Standards appear fundamental for a life-like system to exist. Technical standards are necessary for any complex technology to exist. Technology, the fruit of invention, is basic to the long term development of any human society, and standards brings these fruits to society in a broadly useful form. Prior to the creation of technical standards, technical information, for example tool making, was only passed on by instruction and example. As society becomes more complex, technical standards provide the means to communicate necessary common technical information broadly and uniformly. Standards emerge in each and every human group; the level of standardization (language, writing, number system, monetary system, measurement system, navigational references, communications systems, etc.) in each tribe or society is an indicator of its sophistication and technological attainment. Viewed this way, technical standards appear to be inherent in all complex technical systems, fundamental to almost all forms of commerce and required for more complex communications.

While unit standards may inhibit innovation of competing unit standards, unit standards were a significant factor in the development of early civilization. Taxation provides a more reliable form of state income than tribute. Unit standards provided the weights and measures used for taxation (by barter) and therefore assisted in the rise of the first great city states of Babylon and Egypt. Reference standards of economic value (currency) are the basis of monetary systems, and expanded commerce from barter to purchase.
Similarity standards emerged during the second great wave of civilization, the industrial revolution, to codify the results of repetitive processes. Initially similarity standards were solely private specifications. The barons of the emerging 18th century industrial age were supportive of “standards” so long as they controlled them. They created rail systems of many different gauges so as to prevent the operation of their competitor’s trains on their right-of-way (tracks).
By the early 19th century, the growing use of mechanized process instigated the powerful concept of interchangeability (the transposition of similar parts). Interchangeability of parts was originally conceived for the rapid repair of guns after a battle. In the earliest systems, interchangeability was possible only among the guns from one manufacturer. In this manner, interchangeability was privately controlled and competition was limited. Examples of private products with interchangeable parts that precluded competition: guns, train track spacing, fire hydrant flanges, custom nuts and bolts.
By the mid 19th century, machine tools and measuring devices had progressed sufficiently that it was practical to create a drawing (specification) and machine parts to match. By using these specifications, multiple companies could manufacture interchangeable parts. These specifications were, in effect, early standards. During the same period, society began to realize the importance of having all train tracks or nuts and bolts or fire hydrant flanges interchangable; the result was the beginnings of the systems for standardization in use today.
Now even products that do not need any form of interchangeability have similarity requirements (public and private) for safety, usage, environment, shipping, etc. Examples include: the standards for emergency exit signs, motor vehicle speed limits, the definition and marking of specific plastics for recycling, or the markings for the transportation of hazardous goods. As these examples suggest, similarity standards, when they represent the minimum admissible attributes relating to public safety, are often referenced in government regulations.
Public utilities or state regulation of private utilities prevent commercial advantage where there is the potential for a "natural monopoly" [5]. Natural monopolies have five characteristics:
Figure 1 identifies three different types of standards documents that are used to define similarity and compatibility standards associated with communications. Device standards most often specify similarity, describing the minimum attributes of the device. Interface standards usually define compatibility, and are implemented by defining the transmitted signals that pass across the interface and using the minimum definition of the receiver functions necessary to ensure compatibility. Wireless air interfaces standards for cellular systems are an excellent example of a compatibility standards. Protocol standards (e.g., X.25, Q.931) are used to define both the transmitter and receiver function at the same time. Protocol standards may have attributes of both compatibility standards and similarity standards. Complex communications systems achieve compatible operation by utilizing multiple interface and/or protocol standards.
| Device Standard
|  |
Public voice and early data communications (telegraph) were recognized to be a public good (e.g., universal service) very early in their development [6]. Early public voice and telegraph communications systems used similar equipment and systems to achieve compatibility. Achieving compatibility by requiring similar equipment is one of the characteristics (#3) identifying a natural monopoly. As public telephone and telegraph companies meet all the characteristics of a natural monopoly, many states determined to control the industry via a public utility or regulated private utility. Data communications evolved through its development and use in large organizations and was not recognized as a public good until recently (i.e., the Internet). IBM pioneered modern data communications systems and developed many proprietary compatibility specifications (under the proprietary system Synchronous Network Architecture), but these, often technically superior, private specifications have been rendered obsolete by the market's desire for public data communications compatibility as exemplified by the Internet. The success of the Internet and the failure of IBM SNA may be partially explained by the perceived value of public compatibility standards rather than proprietary compatibility specifications.
There are three significant ways to create public standards:
Too often, all standards are equated with state control. Reviewing the history of standards, unit and reference standards have required state involvement to achieve wide spread utilization. Similarity standards, when they affect the public good, are often referenced in state regulation. However, products that use compatibility standards evidence greater self-reinforcing effects, the combination of effects that cause product demand to increase with increasing market penetration [8] and therefore require less state enforcement. The need for state participation appears to decline with each later stratum of standards.
Current examples of etiquettes used to negotiate with remote systems include the International Telecommunications Union (ITU) V.8 used by telephone modems to negotiate remote compatible operation with the far-end modem. This is how older and newer telephone modems (e.g., V.34 and V.90) find a common way to communicate. In Group 3 facsimile, the negotiating protocol ITU T.30 is an etiquette that has also been very successfully extended (e.g., from 4800, to 9600, 14400 and 28800 bit/s) for over thirty years. In the IETF, standards track RFC 2543, Session Initiation Protocol (SIP) negotiates multimedia communications. SIP has many properties of an etiquette but includes an operational call signaling protocol which may hinder forward compatibility. The recently completed ITU Digital Subscriber Line (DSL) standards use an etiquette (G.994.1) which maintains backward compatibility with the earlier North American DSL standard T1.413 and is planned to support forward compatibility with future standards G.vdsl (very high rate DSL) and G.shdsl. (single-line high speed DSL) Etiquettes may also be applied to the local interfaces between software processes in a single system to support compatibility over time (upgradeability).
Etiquettes simplify the process of maintaining compatibility between systems. Compatibility is a basic part of connectivity; it is fundamental when communications is considered a necessity rather than an option. Compatibility may be considered in three dimensions:
The use of in-network processing for conversion as suggested by the Active Network model is a difficult form of compatibility to deploy. A similar deployment problem also occurred in ISDN networks where a network conversion system was postulated to support conversions between analog (modems) and digital (ISDN) data communications. But there was little incentive to provide such network conversion systems and the ISDN conversion system was not deployed widely. Similarly, requirements for end user applications that support Active Network functionality don't exist until network nodes that support Active Network functionality exist, the "chicken-or-the-egg" problem. So it is also difficult for Active Network implementations to emerge without incentive. The branded ID concept, discussed below, may offer a means to implement such incentive.
Etiquette standards create new ways to implement, control and add value to communications systems. The negotiation defined by an etiquette can support all types of compatibility, and can also support proprietary enhancements using a standardized way of passing proprietary information. In the etiquette, a character string (or similar) is used to provide concept ownership. In Group 3 facsimile, the standardized way to support proprietary enhancements is called ITU T.30 Non-Standard Facilities (NSF). Each NSF is identified by a unique information sequence: ITU country code (T.35), manufacturer's unique code (registered by an in-country organization) and then any information may be exchanged because the communicating ends have uniquely identified each other. In SIP, a reverse domain name is used to provide the unique identity. Other examples of ways to provide the necessary unique identity currently in use include: ASCII representation of tradenames, Internet domain names and ASCAP (American Society of Composers, Authors and Publishers, ASCAP) requirements. Each of these different unique identifiers, including those in T.30 NSF and SIP, may be considered owned by the organization that implements them, and there is legal precedent to suggest that that such ownership would be legally recognized. These information sequences become the identification that communicating systems use to verify design ownership - a "branded ID." By using the branded ID, the communications equipment manufacturer maintains legal control over any proprietary features that are enabled or transferred after the branded ID.
Understanding the operation of an etiquette and why it must be implemented separately requires an understanding of the etiquette's structure. A proper etiquette is an independent protocol containing the etiquette revision level, the parameters the etiquette is negotiating: a listing of protocols supported and associated revision level and options of each protocol, this is followed by any proprietary enhancements (beginning with a branded ID). Etiquettes require an unambiguous tree structure in priority order to ensure that revisions remain fully backward compatible. Using an unambiguous tree structure ensures that additions are always proper super-sets. If it were practical to be certain that all changes to an etiquette were a proper super set then any etiquette would not require revision control. Likely this is not practical and the etiquette must transmit a revision level to allow for changes that are not a proper superset of the previous version. Since in the worst case, systems desiring to be fully compatible would need to support all etiquette revision levels, additions to etiquette revision levels should be made with great care. Since operationally functionality is more likely to change, including it in the etiquette is not desirable.
The proprietary enhancements section of the etiquette would include the branded ID, market segmentation fields, and any proprietary enhancements (or a pointer to them). Adding new protocol identifiers to etiquettes allows the support of additional protocols without affecting the compatible operation of existing protocols, as a proper etiquette receiver must ignore what it does not understand. Verifying such transparency is a difficult etiquette conformance testing task. The maintenance of etiquette standards also requires more care than previous strata standards. Etiquette standards will be used for far longer periods than compatibility standards. As example, T.30 in Group 3 facsimile has been used for over 30 years while the various compatibility standards (modems) that T.30 negotiates have changed at least four times. Careful standards maintenance is necessary to ensure that each change is a proper super-set and that revisions are transparent to the installed base.
Over time, desirable proprietary enhancements may become standard and may be added to the standardized parameter sets. Ricoh, a Japanese facsimile machine manufacturer, offered proprietary higher speed G3 facsimile to its corporate customers. Then, years later, higher speed operation similar to what Ricoh pioneered was included in the G3 facsimile standard.
Keeping revisions fully backward compatible in very complex protocol stacks or software processes is currently impossible, because it is not possible to identify or test all the ramifications of a change. Thus changes to add features or fix “bugs” can result in more “bugs.” Since etiquettes can negotiate protocols (including different revisions), it is possible for an etiquette to negotiate the “best” protocol or revision for a specific application. Where multiple choices of protocols or data sets are possible, the logic for choosing may not be obvious. As example, higher data rate is an obvious choice when there is a selection of data rates as is lower error rate when there is a selection of error rates. But when the etiquette offers a choice of both, some applications may give priority to lower error rate rather than higher data rate. Such priorities need to be communicated, and the rules for choice defined, in the etiquette.
As companies develop unique communications features, they can add them to the proprietary enhancements field, as Ricoh did with higher speed facsimile. In this manner, companies can add value yet support compatible communications or interfaces. In the proprietary enhancements field, the use of a branded ID may provide a legal way to control the proprietary enhancement and therefore may represent a new form of intellectual property.
Such enhancements are not limited to allowing private inventions such as higher data rates or better compression. Etiquettes using a branded ID can also control market segments to increase profits by offering specific capabilities to specific market segments. For example, the banking industry may negotiate stronger encryption, the radiologist market may negotiate higher resolution, the wireless market may negotiate better error control. Market segmentation via the etiquette can also be applied to the distribution channel, allowing individual equipment dealers and distributors to automatically poll their specific customers’ equipment for usage billing (e.g., copier market), problem analysis, and maintenance support (automatic ordering of replacement parts). In these automatic polling cases, the etiquette may include the branded ID and perhaps a customer ID added by the machine dealer to uniquely identify their customers.
In summary, the properties of a proper etiquette appear to include:
Session Initiation Protocol (SIP) appears to be the first near-etiquette to be introduced on the Internet. The application layer meta-representation of structured documents such as XML (eXtensible Mark-up Language), along with the optional modules that define sets of tags and attributes, may create a need for other etiquettes (meta-protocols) to negotiate the desired application level data structures between remote systems. The development of etiquettes and the development of Internet based Active Network or mobile agent functionality may also be synergistic. The set of seven etiquette properties may be a helpful construct when considering mobile agent initiation and Active Network negotiation. As example, etiquettes could differentiate between Active Network data flows and programs while supporting both the proprietary (branded ID) functions and authentication mechanisms needed for the widespread acceptance of Active Networks.
The form of ownership associated with etiquettes, is concept ownership. In some respects, the value of concept ownership is already well established. Trademarks, brands, copyrights, even five bars of music (ASCAP requirement) have for some time provided commercial rights to created concepts. Etiquettes provide the mechanism to enable unique and proprietary concepts to be controlled (branded ID) and electronically communicated over public communications systems.
Commercial organizations that create communications products and services and wish to maximize their profits may find etiquettes a new way to profit from the inventor's or innovator's advantage. Etiquettes, by transporting proprietary information, support a new means to achieve monetary gain based on invention or innovation, while supporting the compatibility so necessary for public communications. It is conceivable that much of the current economic interest in the Internet is engendered by a sense of the possibilities that concept ownership - using the Internet as a medium for exchange - may create. The concept of a branded ID transferred via an etiquette is certainly one mechanism to couple concept ownership to the Internet. The branded ID then becomes a new form of intellectual property, offering new and possibly better ways to support private invention and yet accommodate public good in communicating systems. Each new form of ownership (see Table 1) that emerges with a paradigms shift has created enormous increase in the total wealth of society. Etiquettes, by enabling the communications of concept ownership, create similar opportunities for wealth.
Technical standards, once a narrow field closely tied to state control, are emerging as a discipline of their own. Viewing standards in relation to history, communications, technology and value systems, the paradigm shift from sequential to adaptive systems can be seen more clearly, new concepts appear (etiquettes) and new forms of communications products and services can be envisioned. Such insights demonstrate the usefulness of the taxonomy presented. The strata of technical standards illuminates the relationship of standards, technology and society and by doing so provides insight into the future of each.
[2] Mark Shurmer and Gary Lea, Telecommunications Standardization and Intellectual Property Rights: A Fundamental Dilemma?, Standards Policy for Information Infrastructure, MIT Press, 1995. Return to text
[3] H. Aurthur Klein, The World of Measurement, Simon and Schuster, 1974. Return to text
[4] Paul A. David, Some new standards for the economics of standardization in the information age, Economic Policy and Technology Performance, 1987. Return to text
[5] Richard Ely, The Future of Corporations, Harper's New Monthly Magazine, July, 1887. Return to text
[6] History of Engineering and Science in the Bell System 1825-1925, Bell Telephone Laboratories, Inc., 1975. Return to text
[7] A. Rutkowski, Today's Cooperative Competitive Standards Environment for Open Information and Telecommunications Networks and the Internet Standards Making Model, Standards Development and Information Infrastructure Workshop, June, 1994. Return to text
[8] W. Brian Arthur, Self-Reinforcing Mechanisms in Economics, The Economy as an Evolving Complex System, SFI Studies in the Sciences of Complexity, Addison-Wesley Publishing Company, 1988. Return to text
[9] D.L. Tennenhouse and D.J. Wetherall, Towards an Active Network Architecture, Computer Communications Review, Vol. 26 No. 2, April 1996. Return to text
This page was last updated July 31, 2000.